Remote SSH behind a firewall is a common challenge faced by IT professionals, system administrators, and developers. Whether you're managing servers, troubleshooting systems, or simply trying to access a remote machine securely, understanding how to bypass firewall restrictions is essential. This article will guide you through the process of accessing remote SSH behind a firewall while ensuring security and compliance with best practices.
Firewalls are designed to protect networks from unauthorized access, but they can sometimes create obstacles for legitimate users who need to connect to remote systems. In such cases, knowing how to configure SSH properly and use advanced techniques can make all the difference. This guide will cover everything from basic SSH configurations to advanced methods for bypassing firewalls.
By the end of this article, you will have a clear understanding of how to access remote SSH behind a firewall, ensuring both security and efficiency. Let’s dive into the details and explore the tools, techniques, and strategies that will help you overcome these challenges.
Read also:Ed Skreins Love Life A Closer Look At His Wife And Their Journey Together
Table of Contents
- What is SSH?
- Understanding Firewalls
- Basic SSH Configuration
- Advanced SSH Techniques
- Port Forwarding
- Using SSH Tunneling
- Reverse SSH Tunneling
- VPN Alternatives
- Security Best Practices
- Troubleshooting Common Issues
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication between a client and a server. It provides a secure channel over an unsecured network, enabling users to execute commands, transfer files, and manage remote systems without exposing sensitive data.
Key features of SSH include:
- Encryption of data in transit
- Authentication mechanisms like passwords and key pairs
- Support for tunneling and port forwarding
SSH is widely used in IT environments for tasks such as server administration, remote development, and secure file transfers. Its versatility and security make it an indispensable tool for professionals working with remote systems.
Understanding Firewalls
Firewalls are security systems designed to monitor and control incoming and outgoing network traffic based on predetermined rules. They act as barriers between trusted and untrusted networks, protecting systems from unauthorized access and potential threats.
Types of Firewalls
There are several types of firewalls, each with its own method of operation:
- Packet Filtering Firewalls: Analyze packets and allow or block them based on predefined rules.
- Stateful Firewalls: Track the state of active connections and make decisions based on context.
- Proxy Firewalls: Act as intermediaries between clients and servers, masking the client's identity.
Firewalls often block SSH traffic by default, especially on non-standard ports, to prevent unauthorized access. Understanding how firewalls work is crucial for configuring SSH connections that can bypass these restrictions.
Read also:Peter Zeihan The Man Behind The Global Affairs Expertise And His Role As A Husband
Basic SSH Configuration
Before diving into advanced techniques, it’s important to ensure that your SSH setup is properly configured. This involves configuring both the SSH client and server to allow secure connections.
Configuring the SSH Server
On the server side, you need to modify the SSH configuration file, typically located at /etc/ssh/sshd_config. Key settings include:
- Port: Change the default port (22) to a non-standard port to reduce the risk of automated attacks.
- PermitRootLogin: Disable root login to enhance security.
- PasswordAuthentication: Disable password-based authentication and use key pairs instead.
Configuring the SSH Client
On the client side, you can use the ~/.ssh/config file to simplify connections. For example:
Host myserver HostName 192.168.1.10 Port 2222 User admin IdentityFile ~/.ssh/id_rsa
This configuration allows you to connect to the server using a simple command: ssh myserver.
Advanced SSH Techniques
When basic configurations are not enough, advanced SSH techniques can help you bypass firewall restrictions and establish secure connections.
Using SSH Key Pairs
SSH key pairs provide a more secure alternative to password-based authentication. To generate a key pair:
- Run the command:
ssh-keygen -t rsa -b 4096 - Copy the public key to the server:
ssh-copy-id user@server - Disable password authentication in the server configuration.
Changing the Default Port
Firewalls often block traffic on the default SSH port (22). Changing the port to a non-standard value can help bypass these restrictions. For example:
Port 2222
Remember to update your firewall rules to allow traffic on the new port.
Port Forwarding
Port forwarding allows you to redirect traffic from one port to another, enabling SSH connections even when the default port is blocked.
Local Port Forwarding
Local port forwarding redirects traffic from a local port to a remote server. For example:
ssh -L 8080:remote-server:80 user@ssh-server
This command forwards traffic from port 8080 on your local machine to port 80 on the remote server.
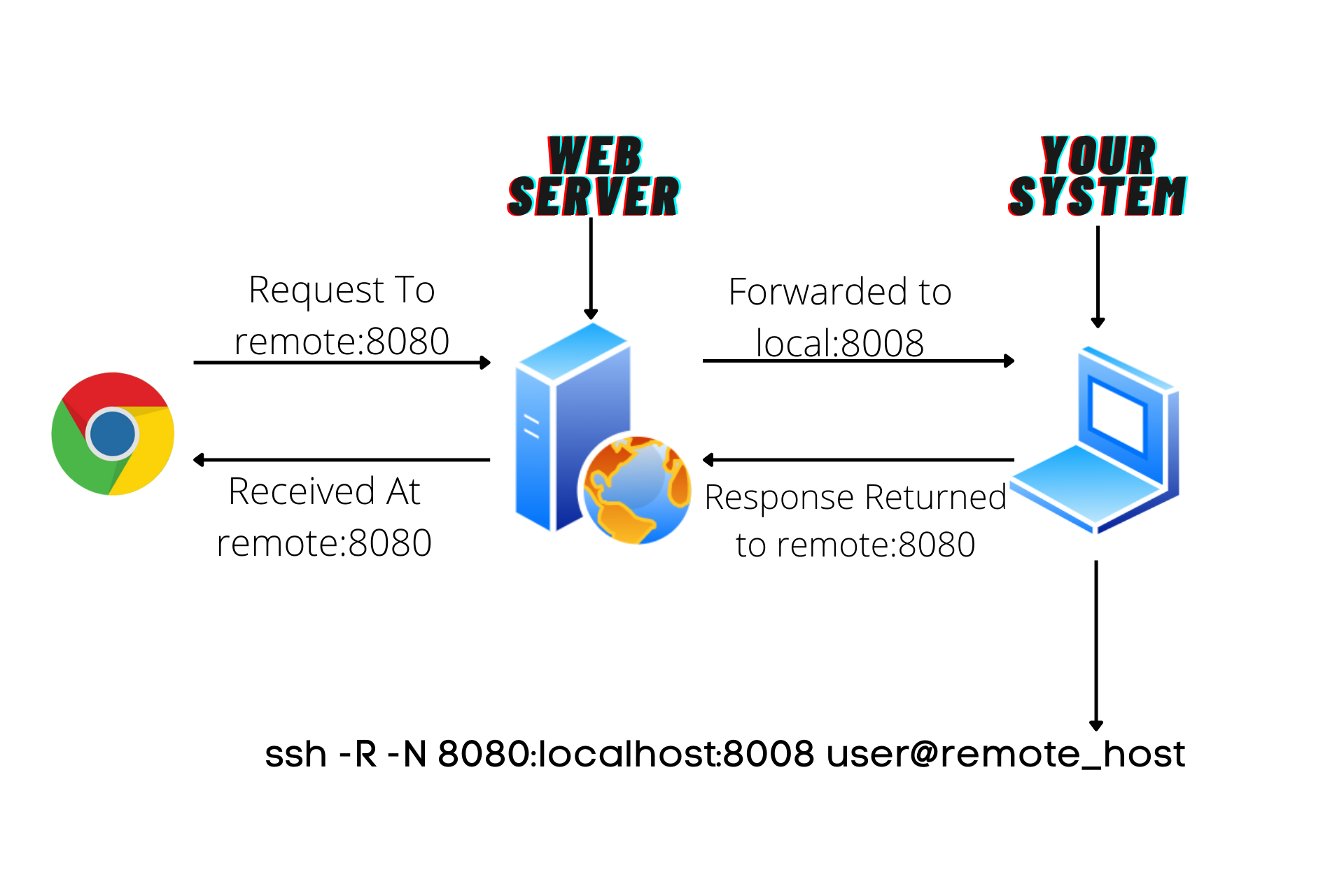
Remote Port Forwarding
Remote port forwarding redirects traffic from a remote server to your local machine. For example:
ssh -R 8080:localhost:80 user@ssh-server
This command forwards traffic from port 8080 on the remote server to port 80 on your local machine.
Using SSH Tunneling
SSH tunneling creates an encrypted connection between two systems, allowing you to bypass firewall restrictions and securely access remote resources.
Dynamic Port Forwarding
Dynamic port forwarding creates a SOCKS proxy that can route traffic through the SSH connection. For example:
ssh -D 1080 user@ssh-server
This command sets up a SOCKS proxy on port 1080, which you can configure in your browser or application settings.
Using SSH Tunneling for Web Access
SSH tunneling can also be used to access web applications securely. For example:
ssh -L 8080:web-server:80 user@ssh-server
This command forwards traffic from port 8080 on your local machine to the web server, allowing you to access it via http://localhost:8080.
Reverse SSH Tunneling
Reverse SSH tunneling allows you to access a machine behind a firewall by initiating the connection from the internal network. This technique is particularly useful for accessing systems that are not directly reachable from the internet.
Setting Up a Reverse SSH Tunnel
To set up a reverse SSH tunnel:
- Run the following command on the internal machine:
ssh -R 2222:localhost:22 user@external-server - Connect to the internal machine from the external server:
ssh -p 2222 user@localhost
Use Cases for Reverse SSH Tunneling
Reverse SSH tunneling is commonly used for:
- Accessing devices behind NAT
- Managing remote servers in restricted environments
- Providing remote support to clients
VPN Alternatives
While SSH tunneling is a powerful tool, there are other methods for accessing remote systems behind a firewall. One popular alternative is using a Virtual Private Network (VPN).
Advantages of Using a VPN
VPNs provide several benefits, including:
- Encrypted communication across the entire network
- Access to multiple resources on the remote network
- Centralized management and control
Setting Up a VPN
To set up a VPN, you can use tools like OpenVPN or WireGuard. These tools allow you to create a secure tunnel between your local machine and the remote network.
Security Best Practices
When working with SSH and bypassing firewalls, it’s important to follow security best practices to protect your systems and data.
Use Strong Authentication
Always use strong passwords and SSH key pairs for authentication. Avoid using default credentials and regularly rotate keys.
Limit Access
Restrict SSH access to specific IP addresses or networks using firewall rules. This reduces the risk of unauthorized access.
Monitor Logs
Regularly review SSH logs to detect and respond to suspicious activity. Tools like Fail2Ban can help automate this process.
Troubleshooting Common Issues
Despite careful configuration, you may encounter issues when accessing remote SSH behind a firewall. Here are some common problems and their solutions.
Connection Refused
If you receive a "connection refused" error, check the following:
- Ensure the SSH service is running on the server.
- Verify that the correct port is open on the firewall.
- Check for typos in the connection command.
Timeout Errors
Timeout errors can occur due to network issues or incorrect firewall rules. To resolve:
- Test the connection using tools like
pingortraceroute. - Verify that the firewall allows traffic on the specified port.
Conclusion
Accessing remote SSH behind a firewall can be challenging, but with the right tools and techniques, it’s entirely possible. From basic configurations to advanced methods like SSH tunneling and reverse SSH tunneling, this guide has covered everything you need to know to establish secure and reliable connections.
Remember to follow security best practices and regularly review your configurations to ensure both functionality and protection. If you found this article helpful, feel free to share it with others or leave a comment below. For more tips and guides, explore our other articles on remote access and network security.