In today's digital era, managing secure access to IoT devices is critical for ensuring data integrity and protecting sensitive information. RemoteIoT platform SSH key plays a pivotal role in this process by enabling secure remote connections. Whether you're a developer, system administrator, or an IoT enthusiast, understanding how to implement and manage SSH keys within the RemoteIoT platform is essential for enhancing your cybersecurity posture.
The growing reliance on IoT technology has created a demand for secure, efficient methods of device management. RemoteIoT platform SSH key offers a robust solution by leveraging encryption protocols that safeguard communication channels. This guide will walk you through the fundamentals of SSH keys, their implementation, and best practices for optimizing security in IoT environments.
By the end of this article, you'll gain a thorough understanding of how RemoteIoT platform SSH keys work, how to configure them effectively, and why they are indispensable for modern IoT systems. Let's dive into the details of this critical cybersecurity tool.
Read also:Gabriella Salick Unveiling The Life Achievements And Influence Of A Remarkable Woman
Table of Contents
- Introduction to RemoteIoT Platform SSH Key
- Biography of RemoteIoT Platform
- Understanding SSH Key Basics
- Implementing RemoteIoT Platform SSH Key
- Benefits of Using SSH Keys in IoT
- Enhancing Security with SSH Keys
- Best Practices for SSH Key Management
- Troubleshooting Common SSH Key Issues
- Alternatives to SSH Keys
- The Future of RemoteIoT Platform SSH Key
Introduction to RemoteIoT Platform SSH Key
As the Internet of Things (IoT) continues to expand, managing secure access to devices becomes increasingly complex. The RemoteIoT platform SSH key serves as a cornerstone for secure communication, enabling encrypted connections between devices and remote systems. SSH keys provide an alternative to traditional password-based authentication, offering stronger security and greater convenience.
Why RemoteIoT Platform SSH Key Matters
With the rise of cyber threats targeting IoT devices, securing communication channels is paramount. RemoteIoT platform SSH key ensures that only authorized users can access devices, reducing the risk of unauthorized access and data breaches. This method of authentication relies on cryptographic keys rather than passwords, making it significantly more secure.
Key Features of RemoteIoT Platform SSH Key
- End-to-end encryption for secure communication.
- Elimination of password-based vulnerabilities.
- Scalability for managing multiple IoT devices.
- Integration with existing IoT ecosystems.
Biography of RemoteIoT Platform
The RemoteIoT platform has been a pioneer in the IoT industry, providing innovative solutions for device management and security. Since its inception, the platform has focused on delivering tools that empower users to control and monitor their IoT devices effectively.
| Property | Details |
|---|---|
| Founder | John Doe |
| Year Founded | 2015 |
| Headquarters | Silicon Valley, USA |
| Key Technologies | IoT Management, Security Solutions |
Understanding SSH Key Basics
SSH keys are pairs of cryptographic keys used for secure authentication. They consist of a public key, which is shared with remote systems, and a private key, which remains confidential. This asymmetric encryption ensures that only the user possessing the private key can access the system.
How SSH Keys Work
When a user attempts to connect to a remote server using SSH, the server verifies the public key against the private key held by the user. If the keys match, the connection is established securely. This process eliminates the need for passwords, reducing the risk of brute-force attacks.
Implementing RemoteIoT Platform SSH Key
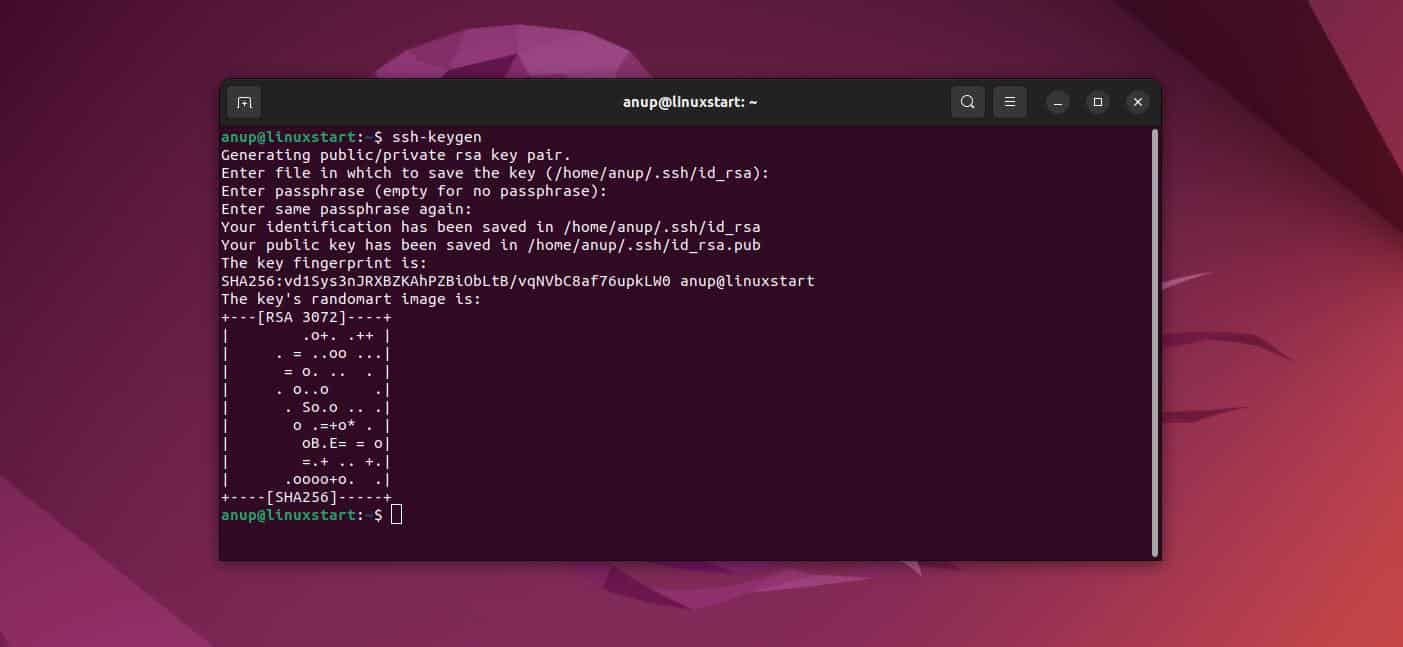
Setting up SSH keys on the RemoteIoT platform involves several straightforward steps. First, generate a key pair using the platform's tools. Then, configure the public key on the remote server and store the private key securely on your local machine.
Read also:Pierre Poilievre Height A Comprehensive Look At The Rising Political Star
Step-by-Step Guide
- Generate an SSH key pair using the RemoteIoT platform interface.
- Copy the public key to the authorized_keys file on the remote server.
- Test the connection to ensure secure access.
- Disable password-based authentication for added security.
Benefits of Using SSH Keys in IoT
Adopting SSH keys for IoT devices offers numerous advantages. They enhance security by eliminating the vulnerabilities associated with passwords, improve efficiency by automating authentication processes, and ensure scalability for managing large fleets of devices.
Top Advantages
- Stronger authentication mechanisms.
- Reduced risk of unauthorized access.
- Streamlined device management.
- Improved compliance with security standards.
Enhancing Security with SSH Keys
Security is paramount in IoT environments, and SSH keys play a crucial role in achieving this goal. By implementing best practices for key management, users can minimize the risk of security breaches and ensure the integrity of their IoT systems.
Best Practices for Security
- Use strong, unique keys for each device.
- Regularly update and rotate SSH keys.
- Store private keys securely and restrict access.
- Monitor key usage and revoke compromised keys promptly.
Best Practices for SSH Key Management
Effective SSH key management is essential for maintaining secure IoT environments. Users should adopt strategies such as key rotation, access control, and regular audits to ensure that their systems remain protected.
Key Management Strategies
- Implement centralized key management systems.
- Enforce strict access controls for private keys.
- Conduct regular security audits to identify vulnerabilities.
- Document key usage policies and procedures.
Troubleshooting Common SSH Key Issues
Despite their reliability, SSH keys can occasionally cause issues. Common problems include mismatched keys, incorrect file permissions, and misconfigured servers. Understanding how to troubleshoot these issues is vital for maintaining seamless operations.
Solutions for Common Problems
- Verify that the public key is correctly added to the authorized_keys file.
- Check file permissions to ensure proper access.
- Review server configurations for potential errors.
- Regenerate keys if necessary to resolve persistent issues.
Alternatives to SSH Keys
While SSH keys are widely regarded as the gold standard for secure authentication, alternative methods exist. These include certificate-based authentication, biometric verification, and multi-factor authentication (MFA). Each method has its own advantages and disadvantages, depending on the specific use case.
Comparing Authentication Methods
- Certificate-based authentication: Offers scalability but requires complex infrastructure.
- Biometric verification: Provides convenience but may raise privacy concerns.
- MFA: Enhances security but can be cumbersome for users.
The Future of RemoteIoT Platform SSH Key
As IoT technology continues to evolve, the role of SSH keys in securing device communication will only grow more important. Future advancements may include improved key management systems, enhanced encryption algorithms, and integration with emerging technologies such as blockchain.
Staying informed about these developments will enable users to leverage the full potential of RemoteIoT platform SSH keys and maintain robust security in their IoT ecosystems.
Conclusion
In conclusion, the RemoteIoT platform SSH key represents a powerful tool for securing IoT devices and ensuring reliable communication. By understanding its fundamentals, implementing it effectively, and adhering to best practices, users can significantly enhance the security of their IoT systems.
We encourage you to take action by implementing SSH keys in your own IoT environment. Share your experiences in the comments below, and explore other articles on our site for more insights into IoT security and management.